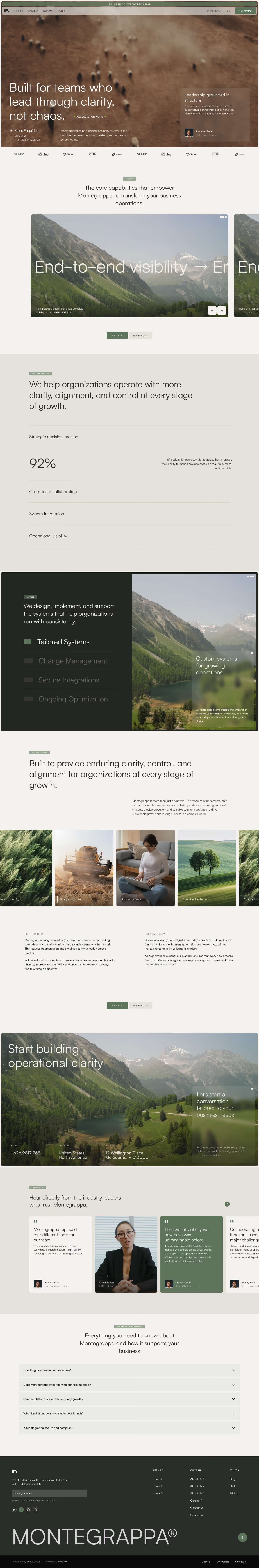
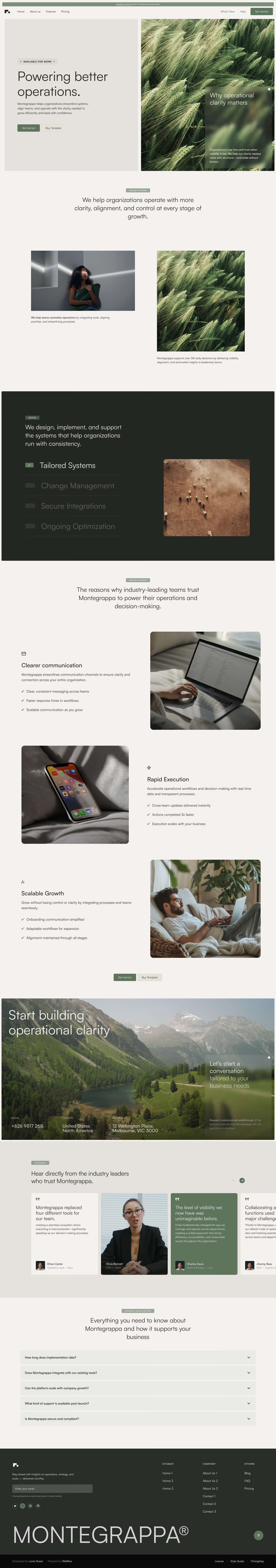
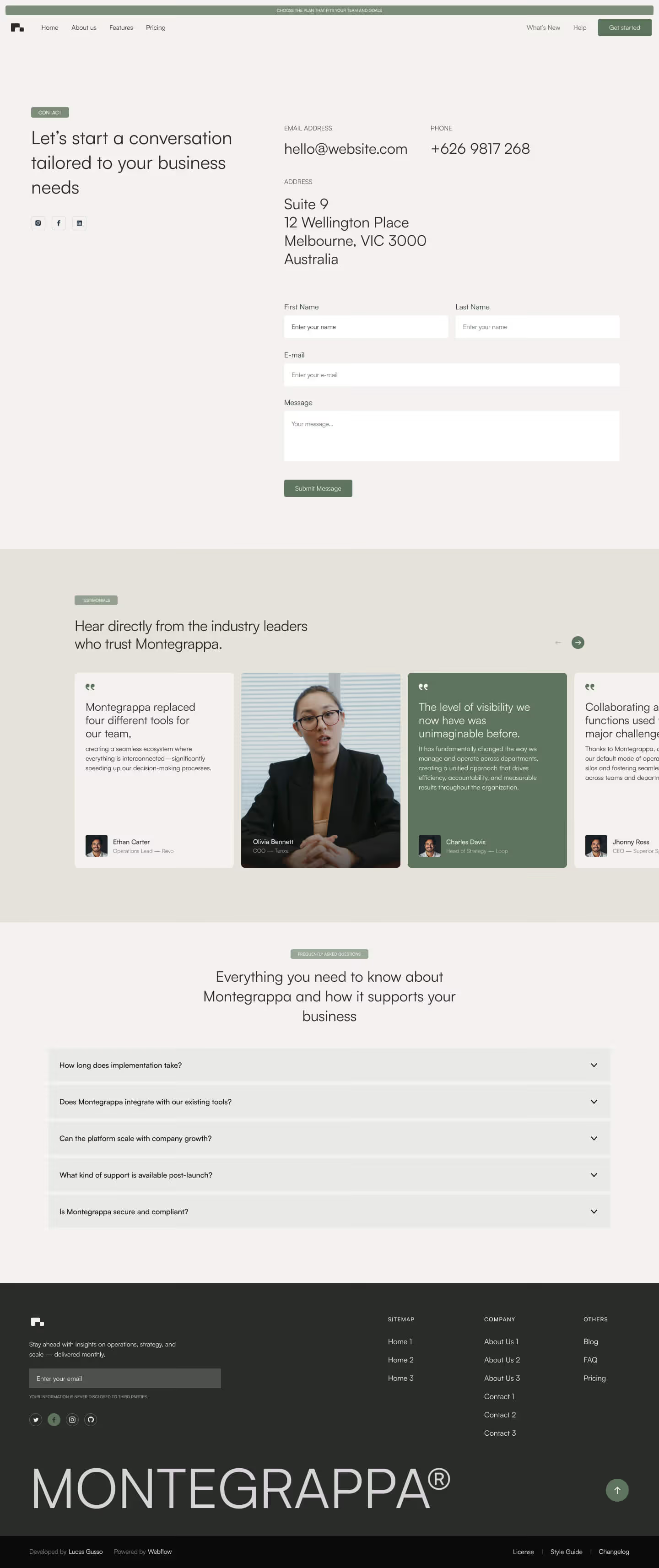
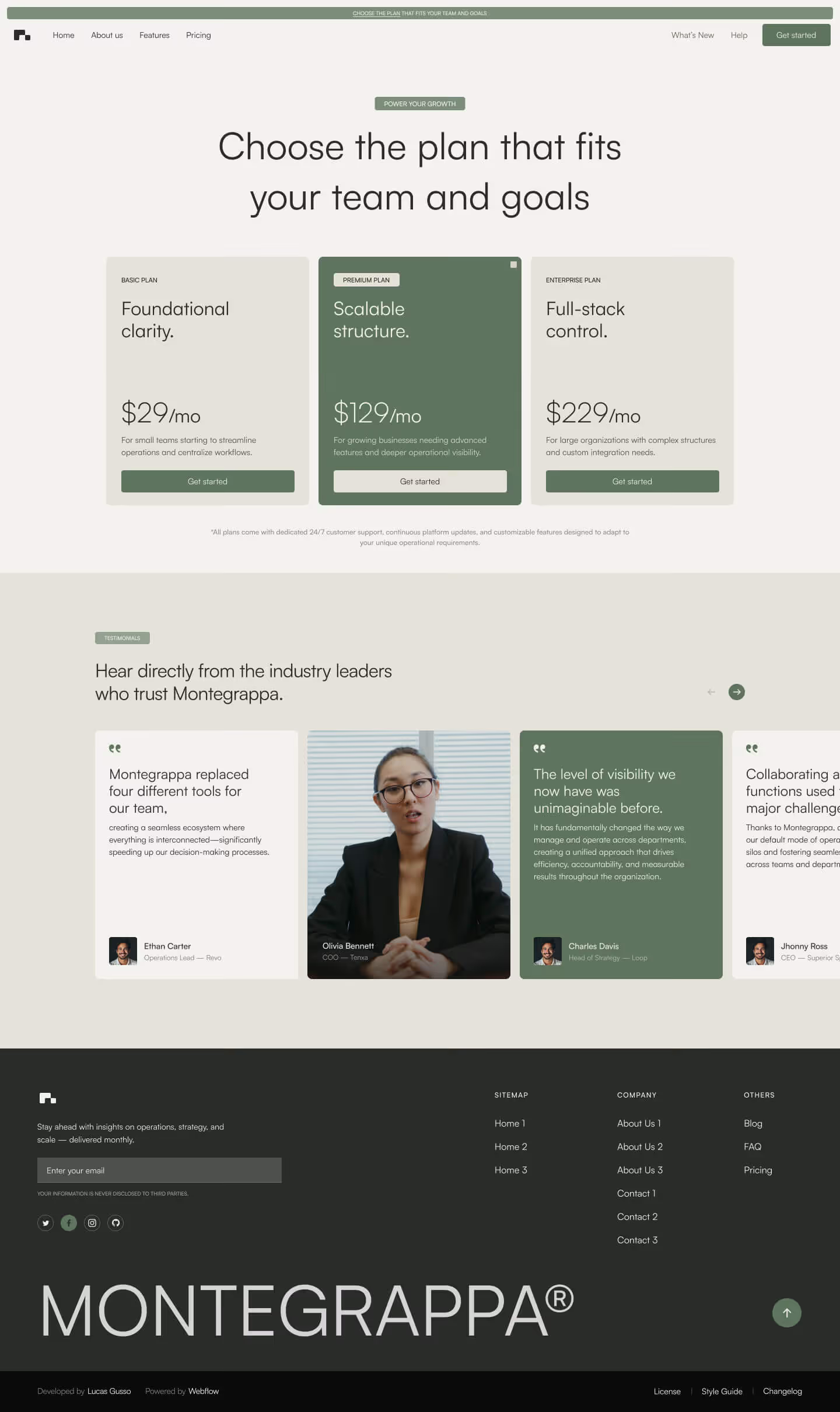
Get a closer look at every layout included in the Montegrappa Template. Each homepage variation is designed for clarity, flexibility, and performance—so you can choose the one that best fits your needs.
Send us an email to lucas.gusso@gmail.com with your purchase receipt, and we will send you the editable Figma file for the Montegrappa Template.
Data processing agreement
Last updated: 06/02/2026
This Data Processing Agreement (“DPA”) forms part of the agreement between Aphy AG (“Processor” or “Aphy”) and the Customer (“Controller” or “Customer”) under which Aphy provides the Services (the “Agreement”).
1. Definitions
“Personal Data”, “Processing”, “Controller”, “Processor”, “Supervisory Authority” have the meanings set out in the GDPR. “Swiss Data Protection Laws” means the Swiss FADP and related ordinances.
2. Roles and Scope
2.1 Roles.
Customer is the Controller of Customer Personal Data. Aphy processes Customer Personal Data as Processor on behalf of Customer.
2.2 Instructions.
Aphy will process Customer Personal Data only on documented instructions from Customer, including as necessary to provide the Services and as set out in the Agreement and this DPA, unless required by applicable law.
3. Details of Processing
The details required by Article 28(3) GDPR are set out in Annex 1 (Processing Details).
4. Confidentiality
Aphy ensures that persons authorized to process Customer Personal Data are bound by confidentiality obligations.
5. Security Measures
5.1 Aphy implements appropriate technical and organizational measures to protect Customer Personal Data, as described in Annex 2 (Security Measures).
5.2 Customer is responsible for secure configuration of its account, user access, and credentials.
6. Subprocessors
6.1 Authorization.
Customer authorizes Aphy to engage subprocessors listed in Annex 3 (Subprocessors).
6.2 Changes.
Aphy will provide notice of new subprocessors via email or platform at least 30 days in advance. Customer may object on reasonable data protection grounds within 14 days. If the parties cannot resolve the objection, Customer may terminate the affected Services.
6.3 Flow-down.
Aphy will impose data protection obligations on subprocessors that are no less protective than this DPA.
7. International Transfers
Where Customer Personal Data is transferred outside the EEA/Switzerland, Aphy will implement appropriate safeguards (e.g., SCCs) and provide them upon request.
8. Assistance to Customer
Aphy will provide reasonable assistance to Customer with:
- data subject requests (Section 9);
- security and breach obligations (Section 10); and
- DPIAs / prior consultation, taking into account the nature of processing and information available to Aphy (Section 11).
9. Data Subject Requests
Aphy will promptly notify Customer if it receives a request from a data subject relating to Customer Personal Data. Aphy will not respond except on Customer’s instructions, unless legally required.
10. Personal Data Breach
Aphy will notify Customer without undue delay after becoming aware of a Personal Data Breach affecting Customer Personal Data, and will provide information reasonably necessary for Customer to meet its obligations.
11. DPIAs and Prior Consultation
On request, Aphy will provide reasonable information to assist with DPIAs and prior consultations, to the extent required under GDPR and applicable law.
12. Deletion or Return
Upon termination or expiry of the Services, Aphy will, at Customer’s choice and as available under the Services:
- return Customer Personal Data and/or
- delete Customer Personal Data
within 30 days, unless retention is required by law. Backups may be retained for limited periods in accordance with Aphy’s backup policies, and will remain protected.
13. Audits
13.1 Customer may audit Aphy’s compliance with this DPA no more than once per year, with 30 days notice, during normal business hours, and subject to confidentiality and security requirements.
13.2 Aphy may satisfy audit requests by providing relevant third-party audit reports (e.g., SOC2/ISO) when available.
14. Liability
Liability under this DPA will be subject to the limitations of liability in the Agreement, unless prohibited by applicable law.
15. Swiss Addendum
Where Swiss Data Protection Laws apply:
- references to GDPR include the equivalent provisions under Swiss law;
- “Supervisory Authority” includes the FDPIC where applicable; and
- cross-border transfer safeguards will follow Swiss requirements as well.
16. Order of Precedence
If there is a conflict between this DPA and the Agreement regarding data protection, this DPA prevails.
Annex 1 — Processing Details (Article 28(3) GDPR)
Subject matter: Provision of Aphy platform and related services for hospitality operational workflows (including reporting and automation workflows as configured by Customer).
Duration: For the term of the Agreement plus the retention periods in Section 12.
Nature of processing: Collection, storage, organization, use, transmission, retrieval, deletion.
Purpose: Provide, maintain, secure, and support the Services; implement Customer-configured workflows; provide reporting and operational outputs.
Types of Personal Data (depending on Customer use):
- Guest data: name, nationality, ID/passport details, dates of stay, booking references, contact details (if provided), and other fields required for reporting
- Staff/admin user data: name, email, role, login data
- Operational data: logs, workflow records, status metadata
Categories of data subjects: - Customer staff and authorized users
- Guests and other individuals whose data Customer inputs
Special categories: Not intended. Customer should avoid providing special category data unless necessary and documented; if required, parties will agree additional safeguards.
Processing operations: As above; may include integrations with third-party systems per Customer configuration.
Annex 2 — Security Measures (Baseline)
Aphy maintains appropriate measures, which may include:
- access control and least privilege; MFA for administrative access
- encryption in transit (TLS); encryption at rest where feasible/appropriate
- logging and monitoring
- vulnerability management and patching
- secure development practices
- incident response procedures
- backup and recovery
- subprocessors assessed for security posture
Annex 3 — Subprocessors
- Microsoft Azure - Hosting
- Hetzner - Hosting
- UiPath - Infrastructure